exploits.club Weekly Newsletter 38 - Linux Races, Blind Memory Corruption, LLM Java Fuzzing, and More

Summarize blog posts every week, they said. It will be fun, they said. Annnnnyways👇
In Case You Missed It...
- Your Teammate Isn't Human: Mixing Decompilation and AI for Modern Reverse Engineering - The Keynote for HITCON CMT 2023 hit YouTube a few weeks back, as brought to our attention by the man himself, @mahal0z.
- The Art of Finishing - Get your mind out of the gutter. This one is not VR specific, but we are willing to bet a handful of our readers might struggle with side-project-abandonment-syndrome. This methodology post takes an interesting perspective on how to combat your illness and actually ship your projects.
- OrangeCon Videos Are Live - Watch all the talks from the new Dutch Security Conference.
Resources And Write-Ups From This Week:
- Race conditions in Linux Kernel perf events- Binary Gecko has been on a roll recently with the blog posts. We first covered their Chrome write-up just two weeks ago, and now they are back with a Linux bug they recently disclosed to the kernel security team. The core issue (as the title suggests) is a race condition in perf events that leads to a page reuse primitive. The blog is highly technical, covering all the structs and code paths you need to understand the core issue and the team's exploit.
- Windows WiFi Driver RCE Vulnerability – CVE-2024-30078 - Speaking of teams who have been pushing out blog posts recently, Crowdfense has returned to the interwebs with an RCA and exploitability analysis of CVE-2024-30078. The post starts with a bindiff of the patched WiFi driver and then dissects the code changes. The team identified the bug stems from improper handling of packet data when translating IEEE 802.11 packets to Ethernet packets, which results in a 4-byte overflow. The blog then talks through the limitations of this bug, ultimately deciding it may not be critical/exploitable but eager to be proved wrong.
- Deep Dive into RCU Race Condition: Analysis of TCP-AO UAF (CVE-2024–27394) - A new post out of Theori this week walks through a different Linux race-condition leading to UAF. The bug happens during the TCP Authentication Option connection initiation and stems from improper usage of the Read-Copy-Update API (which the post covers at length). To reliably win the race, the team leveraged ExpRace, which was initially presented at USENIX '21.
- CVR: The Mines of Kakadûm - Google's Cloud Vulnerability Research team took to the BugHunter blog to discuss their research on exploiting memory corruption bugs in server-side libraries under unknown execution environments. Specifically, the post focuses on Kakadu, a JPEG 2000 library. The post goes over the technical details of the software before walking through the team's vulnerability research methodology. The team discovered two vulnerabilities - an OOB write and an arbitrary file read. They leveraged the file read to obtain information about the execution environment and trigger "Conditional Corruption." After that, they used the OOB write to modify global variables and hijack control flow. The post is super in-depth, discussing a handful of roadblocks the team encountered - certainly worth a full read-through.
- Veeam Backup & Response - RCE With Auth, But Mostly Without Auth (CVE-2024-40711) - Watchtowr and enterprise software go together like white-on-rice. This week, they took a stab at a recently reported critical vuln in Veeam Backup and Response, CVE-2024-40711. The post starts with a patch diff, where they identify that a well-known deserialization gadget has been added to the blacklist. From there, it's off to the races with an overview of Veeam's .NET remoting internals, a deep...deep dive into the interesting code paths, and finally, some .NET deserialization goodies. The post finishes with an overview of the silent authentication patch the team implemented, making the advisory slightly confusing. And while you are on Watchtowr's blog, you should also take a look at the post they put out yesterday about becoming admins of .mobi.
- A journey through KiUserExceptionDispatcher - Who doesn't love a good emulator dev post? @momo5502 wrote up some of his recent findings and struggles in this devlog-style post about his battles with Exceptions while building his user-space emulator. This required quite a bit of reversing of
KiUserExceptionDispatcherto understand how to implement a proper stack layout. It's a fun post that makes you want to break out your code editor and IDA. - angr for real-world use cases - Chances are pretty high that you've encountered a CTF write-up where the author did some angr-fu and blew you away. However, there are some limitations when leveraging the tool in real-world research. Thankfully, @volodiyah is here to help you overcome some of those hurdles so you can add a new tool to your tool belt. Ignoring the Vim slander, you will find a handful of helpful tips in this post, from how to use angr to collect accurate time code coverage, how to improve your debugging workflow, and how to add support for Window's debugging symbols.
- Introducing Java fuzz harness synthesis using LLMs - OSS-Fuzz is back to talk about their ongoing LLM harness generation project. This time, the team has been focusing on how the project has been extended to work with everyone's favorite language...Java. The post looks at a Java fuzz harness sample before walking through several challenges associated with auto-generation, such as object construction and exception handling. The team then shows 4 reliability bugs caught with generated harnesses and concludes with some thoughts and ideas for future work.
Interesting Job Postings:
- Junior Vulnerability Researcher via Pedro Ribeiro (Remote)
- Vulnerability Research Intern @ Interrupt Labs (On-Site: Acton, Australia)
- Lead Embedded Systems Vulnerability Researcher @ Nightwing (On-Site: Annapolis Junction, MD)
- Senior Embedded Engineer, Security/Privacy, Pixel @ Google (On-Site:
Warsaw, Poland) - Internship, Product Security Engineer, Vehicle Software (Winter/Spring 2025) @ Tesla
Introducing...Bug Directory:
Last week, we alluded to a project we have been working on in the background. While it's not quite ready for prime time just yet, we wanted to go ahead and give you a few more details...
We have been hard at work doing the challenging, rewarding, and inspiring work of....going through each of the previous exploits.club resources and tagging them. This has allowed us to put together an Open-Source Obsidian Vault that will allow you to explore subsystems, technologies, and primitives in a much quicker and more effective manner.
It will be published on the web through Obsidian Publish and available on GitHub to be cloned and used locally. Even better, that means you can submit PRs for new resources, links, or tags to help out your fellow researchers. The bigger the vault, and the more connections it has, the more useful it becomes. Check-out the demo GIF below 👇
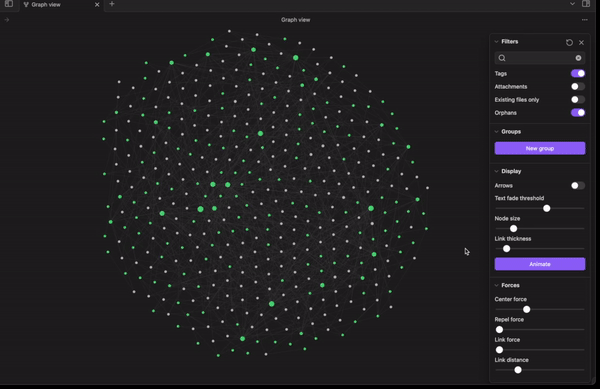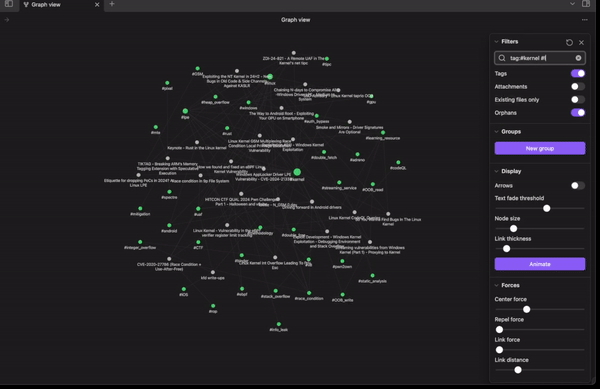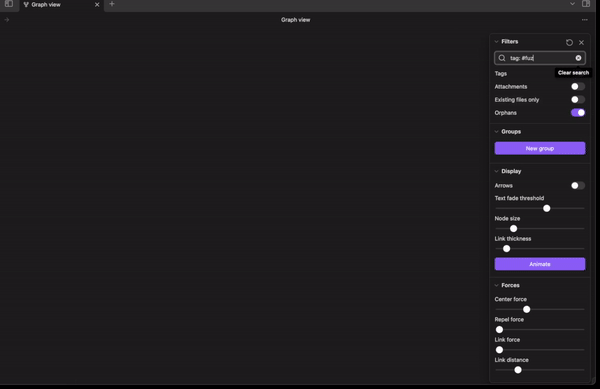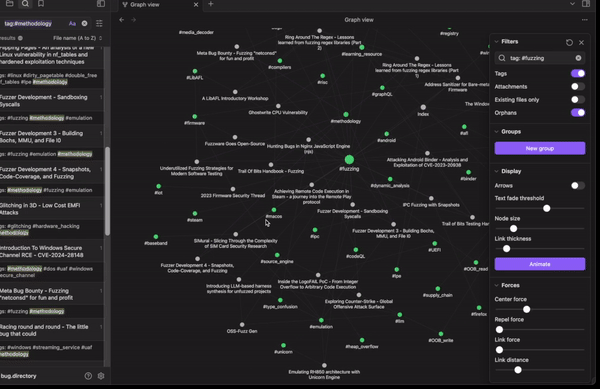
We should be live this week, so monitor X for the official launch
Wrapping Up...
As always, thanks for stopping by. We here at the club are always trying to improve so if you have comments, questions, or suggestions, feel free to shoot us an email - info@exploits.club.
Follow us on X - we occasionally Tweet poor attempts at memes
We sell mugs, and personally we have seen a drastic uptick in bugs since using ours. Get yours on at https://shop.exploits.club.

Feel free to join the exploits.club Discord server here 👉 https://discord.gg/2dxN2Gtgpx
Same time next week? See you then 🏴☠️
